This entry was posted in Vulnerabilities, Wordfence, WordPress Security on August 8, 2017 by Mark Maunder 3 Replies
We have seen a significant increase in the number of websites affected by malware we refer to as ‘TrafficTrade’. This malware is a piece of javascript that an attacker drops into your website content once they have compromised it. Your visitors are then redirected to websites that install malicious browser plugins or serve up spam advertising.
How TrafficTrade infects your website
So far the Wordfence Security Services Team has seen two infection vectors (methods of infection). The first is websites that are infected because they left the searchreplacedb2.php script lying around. This is a relatively uncommon infection vector. We wrote about this risk a few weeks ago.
The second vector is by far the most common. The attackers are exploiting a vulnerability in the WordPress ‘Newspaper’ theme. This vulnerability allows them to inject malicious code into the WordPress ‘wp_options’ table which then redirects your traffic to malicious websites or ad campaigns. Our Security Services Team has seen several other themes that are based on the Newspaper WordPress theme that suffer from the same vulnerability.
Wordfence released a Premium firewall rule about 40 days ago which prevents these attackers from exploiting the Newspaper theme. Even if you had a vulnerable theme, you would have been protected. About 10 days ago, that rule became available to our free customers too.
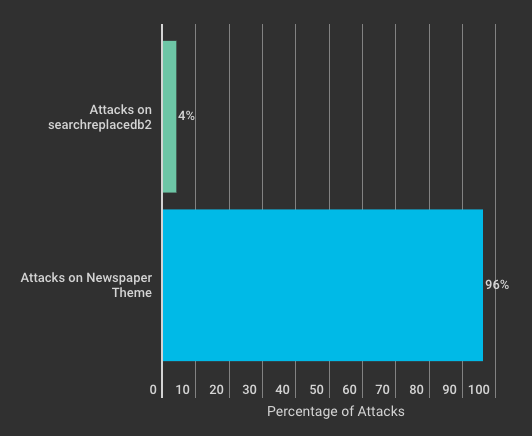
The chart below shows how attacks on the Newspaper theme have completely dominated the distribution. Attacks on searchreplacedb2.php have only been 4% of total attacks over the past few weeks.
How The TrafficTrade.life Attack Campaign has Ramped Up
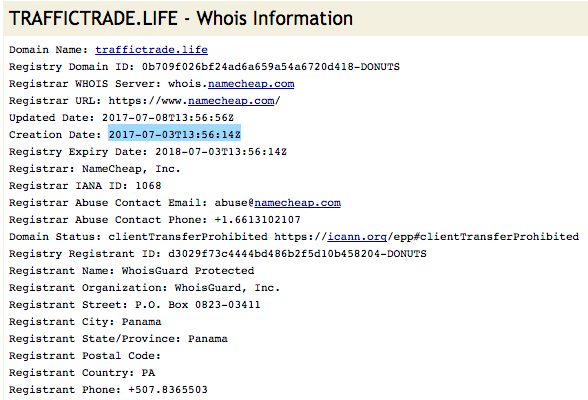
The traffictrade.life domain was registered on July 3rd, a little over 1 month ago. It is protected by WhoisGuard, a Panamanian company that provides domain registration anonymity services.
We started seeing attacks that were attempting to drop malware with a malicious redirect hosted at traffictrade.life starting on July 10th. The total number of attacks per day have ranged from just 1 per day up to as many as 630. Then things really took off in the past week as you can see from the chart below. We started seeing up to 15,000 attacks per day attempting to drop the traffictrade.life malicious redirect.
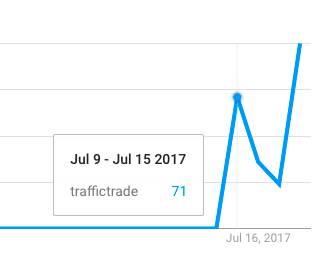
Even Google Trends is showing an increase in search volume for the phrase ‘traffictrade’towards the end of July as attacks ramped up and affected webmasters started searching Google for help:
What to Do To Protect Yourself
As always we recommend running Wordfence Premium. In this case, our Premium customers have been protected for over 40 days from TrafficTrade by a Premium firewall rule that was deployed by our team in real-time.
The firewall rule became available to our free community users about 10 days ago. Both Wordfence free and Premium are now protecting your sites from these attacks.
Because this infection is so wide-spread, we have released additional detection in the Wordfence malware scan to detect a newer variant of TrafficTrade. We are seeing attackers modify your wp_options table to inject the malicious code into that table. A Wordfence scan will now detect this.
This new feature is immediately available for free and Premium Wordfence customers with Wordfence version 6.3.16 which was released this morning. Simply install Wordfence or update to 6.3.16 and run a scan.
What TrafficTrade Malware Does On Your Site
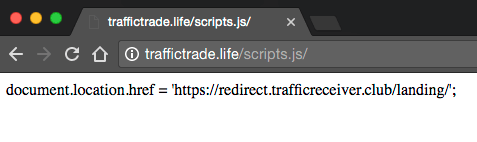
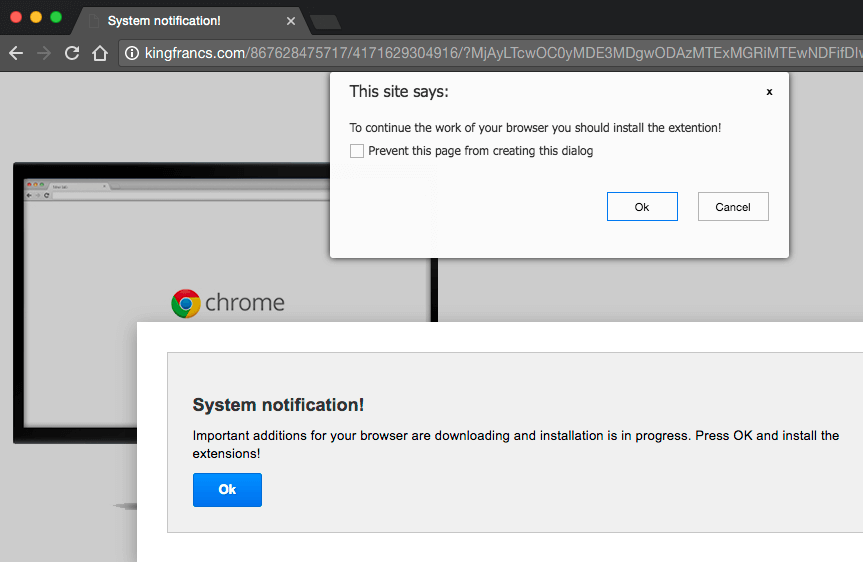
Once you have been infected with TrafficTrade, it injects Javascript onto your site that loads from the TrafficTrade.life domain. The actual script is very simple. If you load the URL manually, it looks like this:
It redirects your visitors to a ‘trafficreceiver’ domain which then does further redirects to whichever campaign they are running. In the case of my test, you are redirected to a site that wants you to install a Chrome plugin – most likely malicious.
Where The Attacks Are Coming From
The majority of attacks that we have intercepted and that are dropping the TrafficTrade malicious redirect code come from four IPs:
- 79.110.128.128 – 13,698 attacks
- 79.110.128.17 – 11,071 attacks
- 79.110.128.63 – 4,798 attacks
- 79.110.128.252 – 607 attacks
We are seeing attacks originating from several hundred other IPs, but the numbers are very low – ranging from single to double digits. The above IPs are by far the top offenders.
The above IPs belong to UnderNet LLC, based in Kiev in Ukraine. They are part of a block of 2048 IP addresses in the range 79.110.128.0 – 79.110.135.255.
UnderNet LLC’s website is at under.net.ua. This is a snapshot of their home page:
A Change In Hosting and Tactics on July 31st
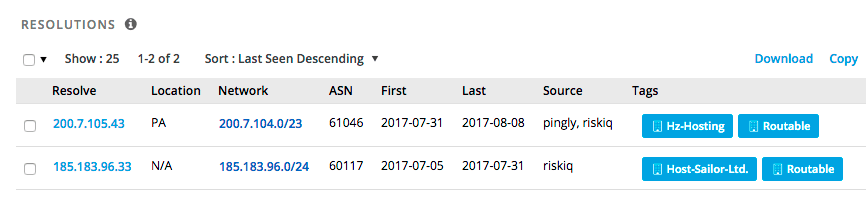
The threat actors behind the TrafficTrade campaign were using a well known “bulletproof” hosting company to host traffictrade.life until July 31st. They were based at HostSailor with servers in the Netherlands, which Brian Krebs has written about in depth in August 2016. According to Krebs, HostSailor has a long history of hosting malicious content and services, as does their owner.
On July 31st, the campaign switched their primary domain IP address as they also switched tactics. The IP address that the traffictrade.life domain pointed to, changed from 185.183.96.33 hosted at HostSailor in the Netherlands to 200.7.105.43 which is hosted by “HZ Hosting Ltd”, also known as HostZealot.
The HostZealot website is at www.hostzealot.com and the company is based in Plovdiv in Bulgaria.
On July 31st we also saw a change in tactics. The attackers switched from trying to exploit searchreplacdb2.php to exploiting the Newspaper Theme in WordPress. The number of attacks we saw also ramped up significantly on July 31st when that domain IP change occurred. We saw 15,000 attacks on a single day.
When the attackers switched to HostZealot, they immediately ramped up attacks to 15,000 per day as the graph below shows.
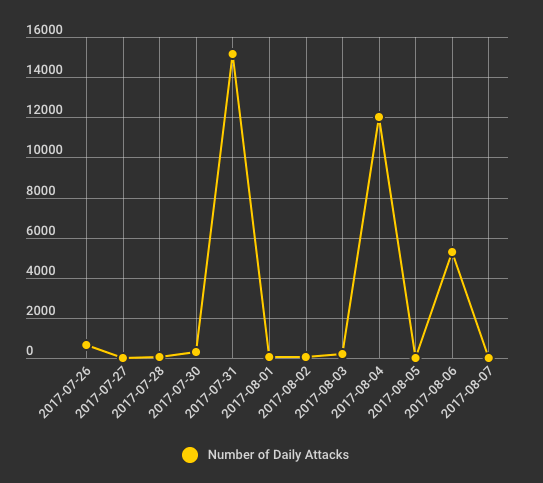
The threat actors behind TrafficTrade may have switched away from HostSailor because it is blacklisted by many security companies and firewalls online, including Wordfence. Switching to a lesser known bulletproof host may have allowed them to bypass some blacklists with their attack campaign.
Spread The Word
The Wordfence team has seen a wide impact from this malware. Many of our site cleaning customers have been hit by this. We have also seen a significant rise in the number of infection attempts during the past few days.
We are not isolated in observing this infection. Dan Fennel wrote about this on July 24th. This is showing up on StackOverflow (July 17th). And we initially covered this on July 25th when we wrote about the risks of searchreplacedb2.php – although at the time we didn’t realize the attack would become so prolific starting July 31st.
To help protect the WordPress and online community, please share this with your friends and colleagues.
Thanks to Brad Haas and Dan Moen for their assistance and contributions to post.
Mark Maunder – Wordfence Founder/CEO.